Blockchain: A Novice’s Guide to this Technology

Blockchains are incredibly popular nowadays, but what is a blockchain, how do they work and what problems can they solve and how can they be used.
As the name implies, a Blockchain is a chain of blocks that contain information. This technique was originally described in 1981 by a group of researchers and was intended to timestamp documents so they couldn’t be backdated or tampered with, almost like a notary.

However, it remained mostly unused until Satoshi Nakamoto adopted it in 2009 to create a digital cryptocurrency called Bitcoin.
Now, a Blockchain is a transparent, secure and decentralized ledger that is completely opened to anyone.
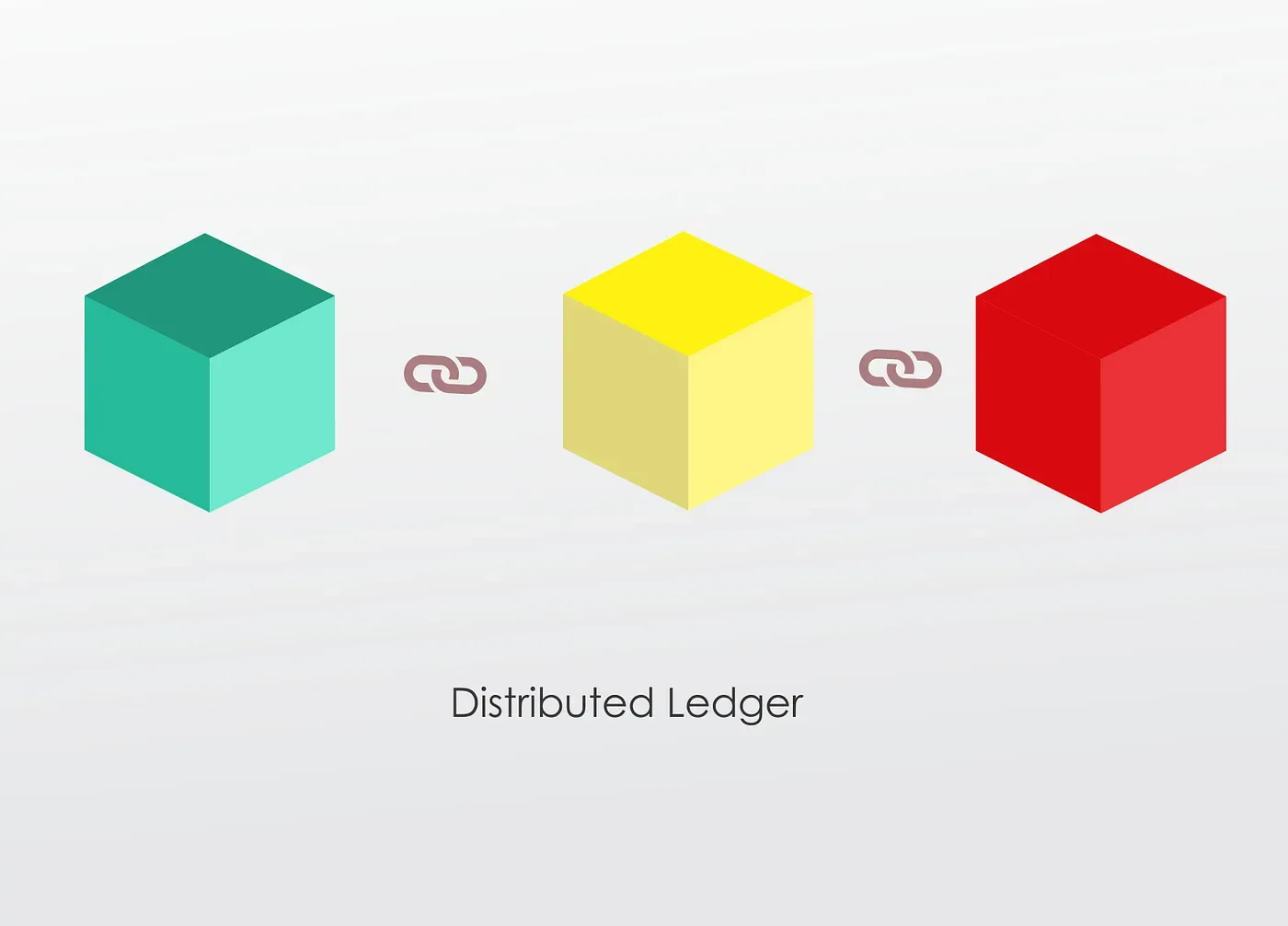
They have an interesting property, once some data has been recorded inside the blockchain it becomes very difficult to change it.
How Does a Blockchain Work on a Basic Level?
Let’s take a closer look at a “block”. A block contains Data, Hash, and Hash of the previous block.
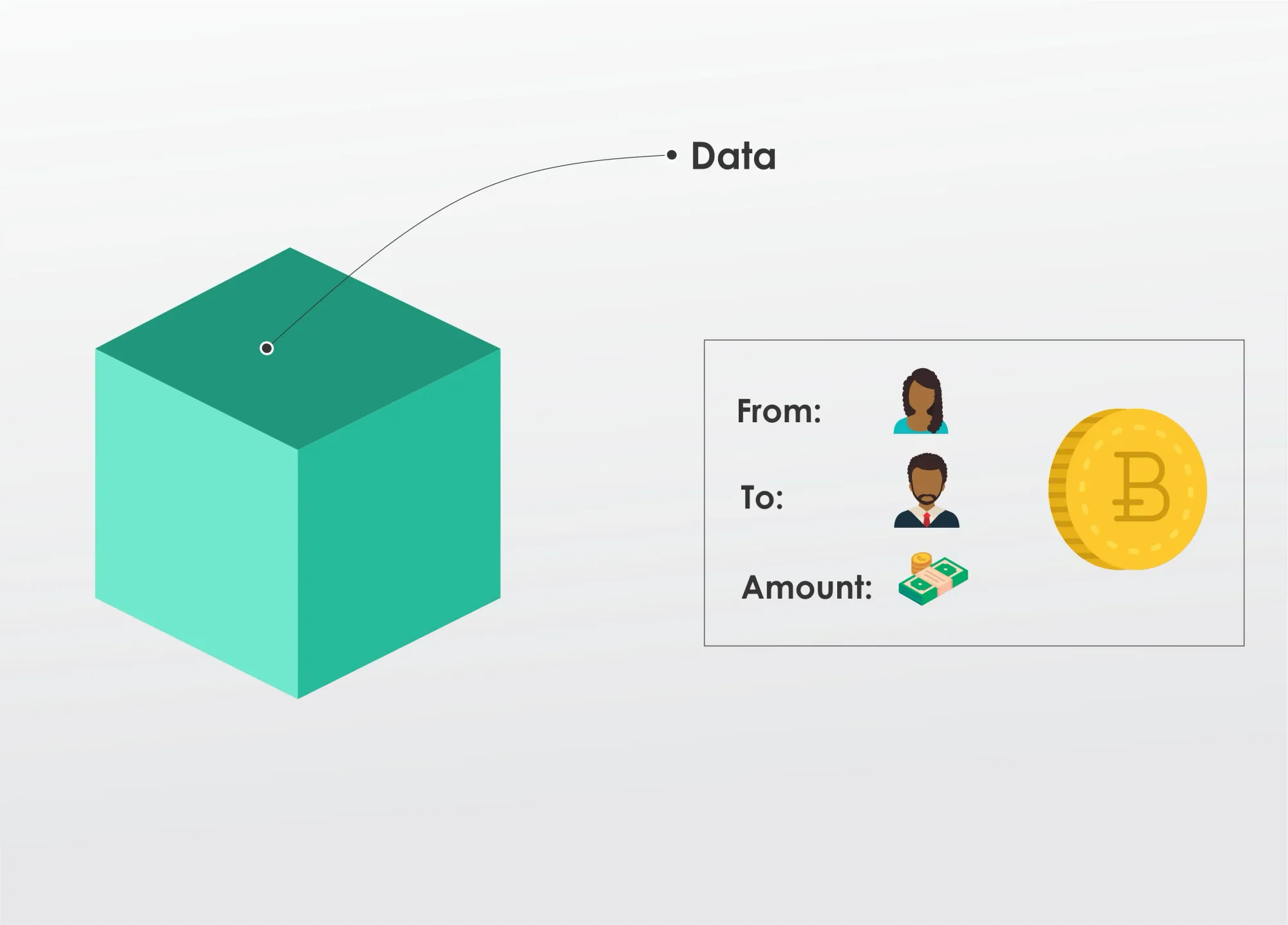
Data
Each block contains some data, the hash of the block, and the hash of the previous block.
The data stored in the block depends on the type of blockchain. The “Bitcoin Blockchain,” for example, stores the details about a transaction, such as the sender, receiver, and the number (amount) of coins.
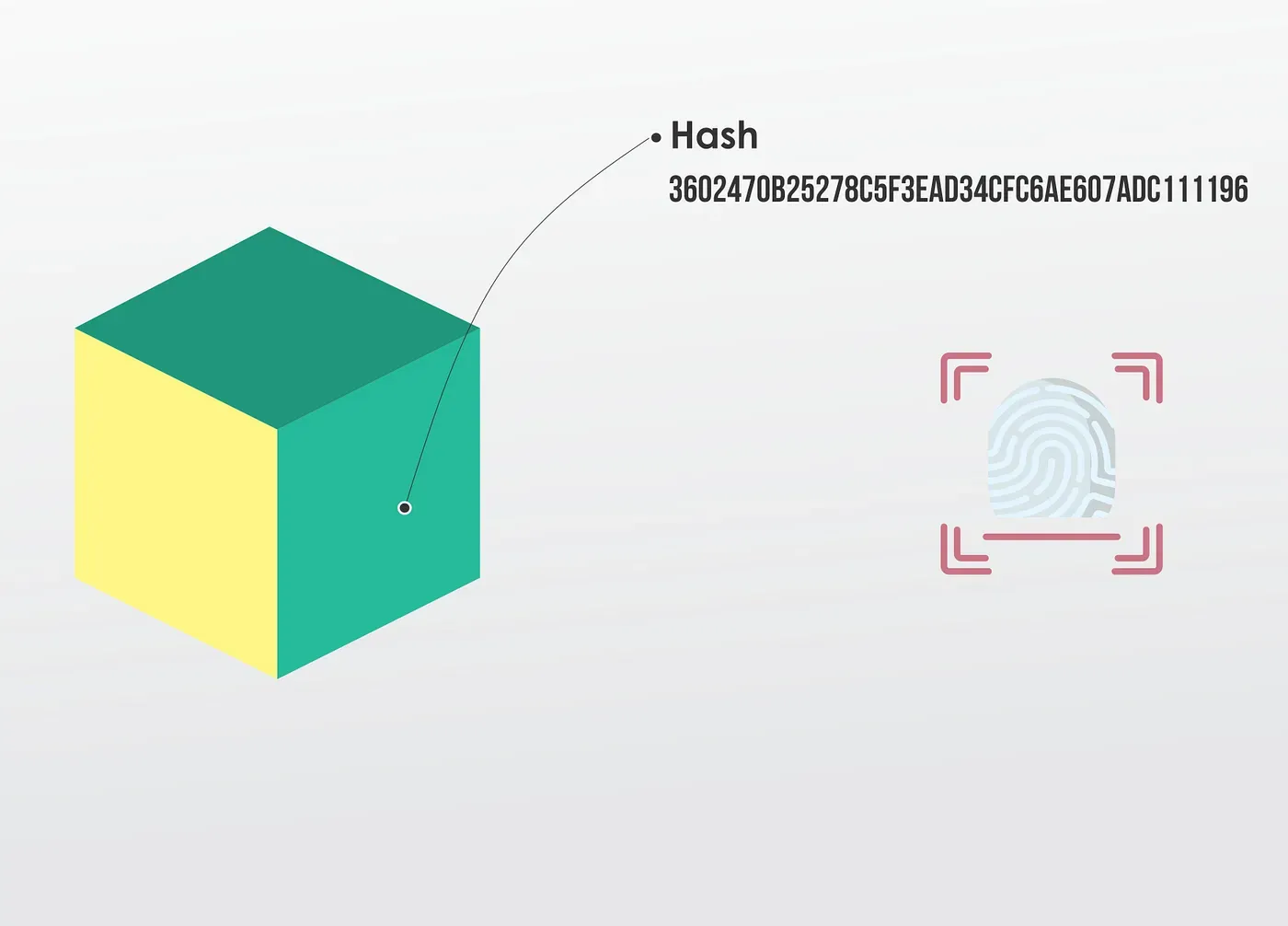
Hash
A Block also has a Hash. You can compare a hash to a fingerprint; it identifies a block and all of its contents, and it’s always unique, just like a fingerprint.
Press enter or click to view image in full size
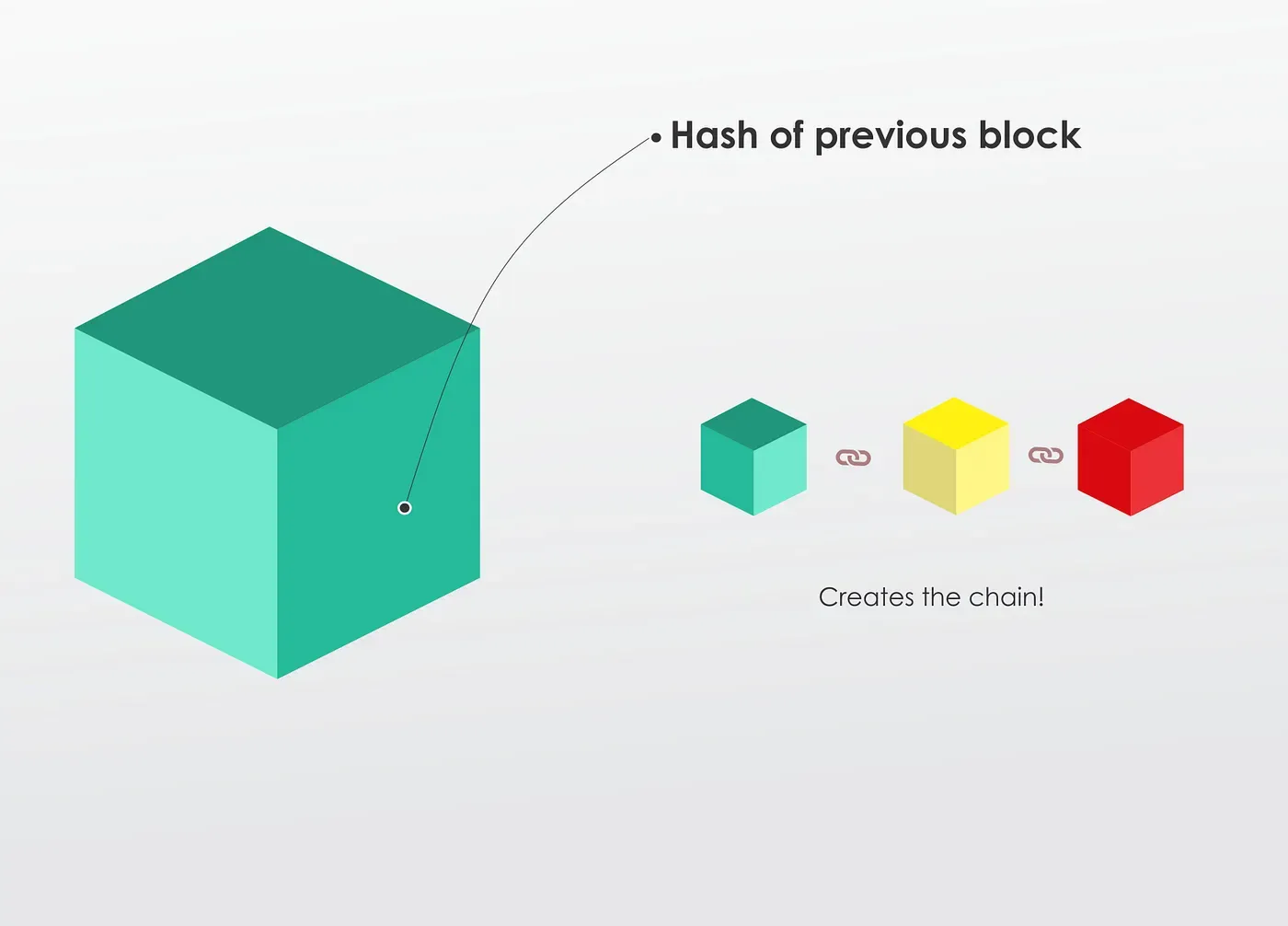
Once a Block is created, its hash is calculated. Changing something within the Block will change the hash. So, in other words, hashes are very useful when you want to detect changes to blocks. If the fingerprint of a block changes, it is no longer the same block.
Hash of Previous Block
The third element inside each block is the hash of the previous block. This effectively creates a chain of blocks, and it’s these techniques that make blockchain so secure.
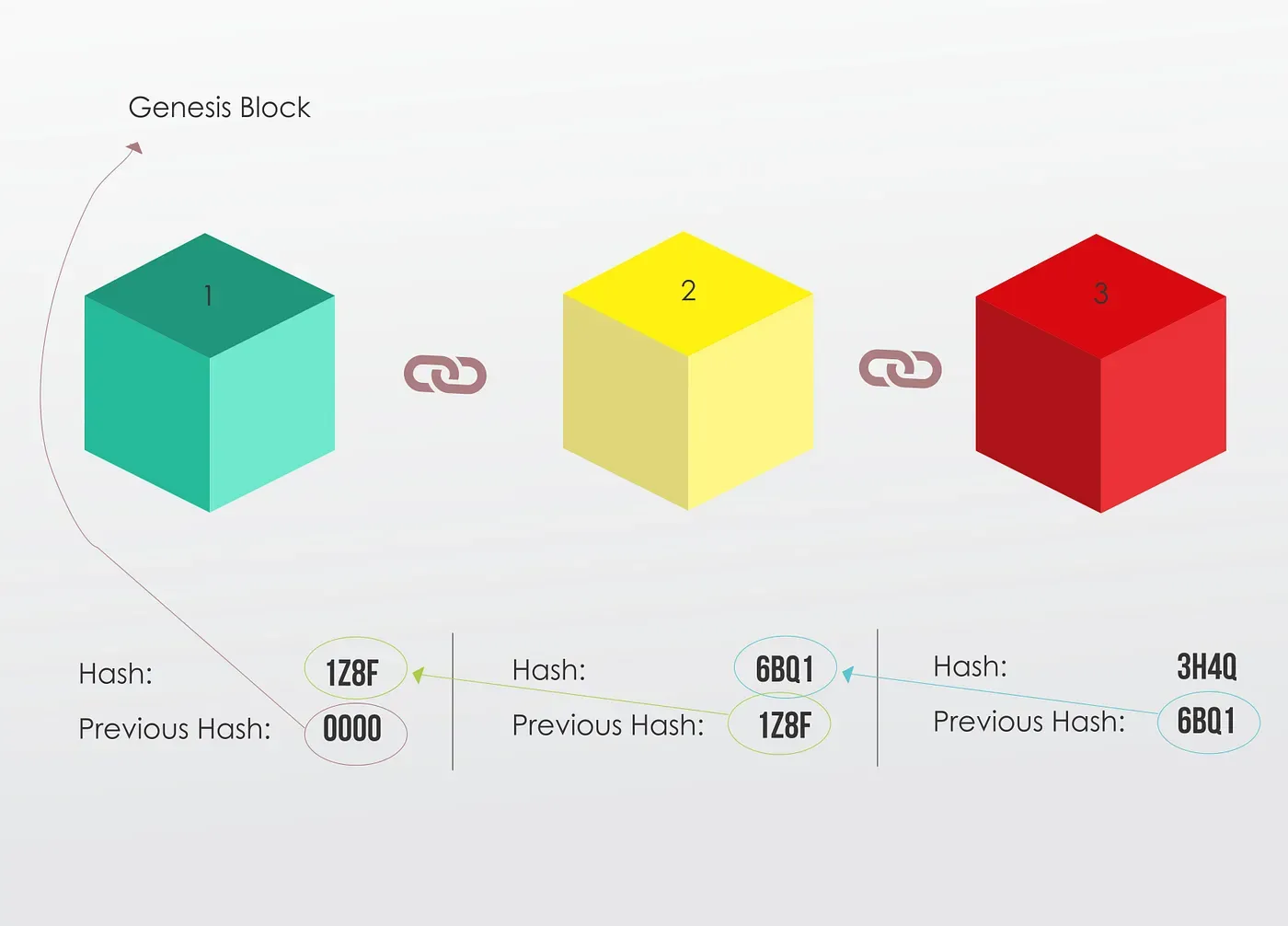
Let’s take an Example
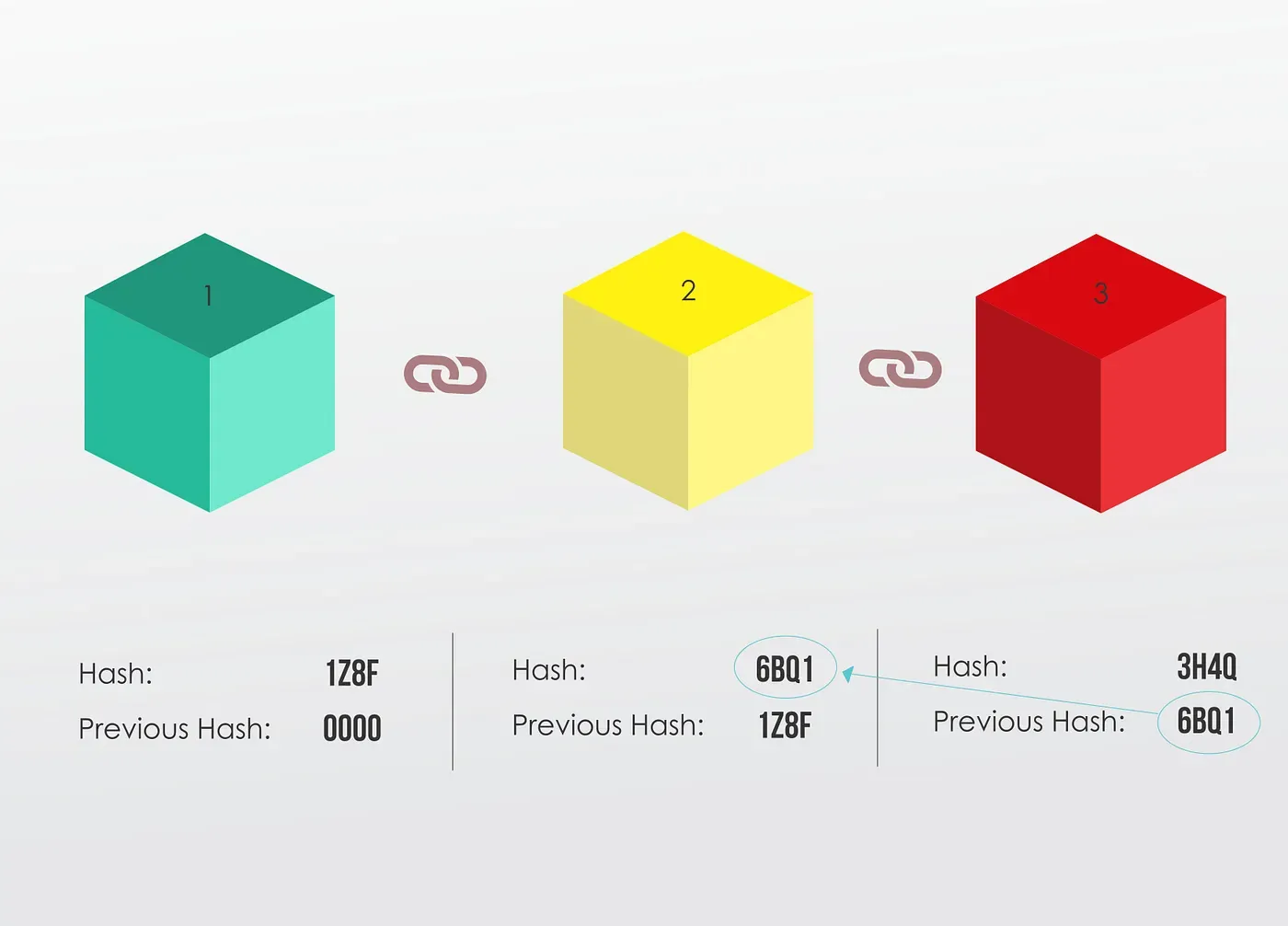
Here, we have three (3) blocks, as you can see each block has a hash and the hash of the previous block.
So block number 3 points to block number 2
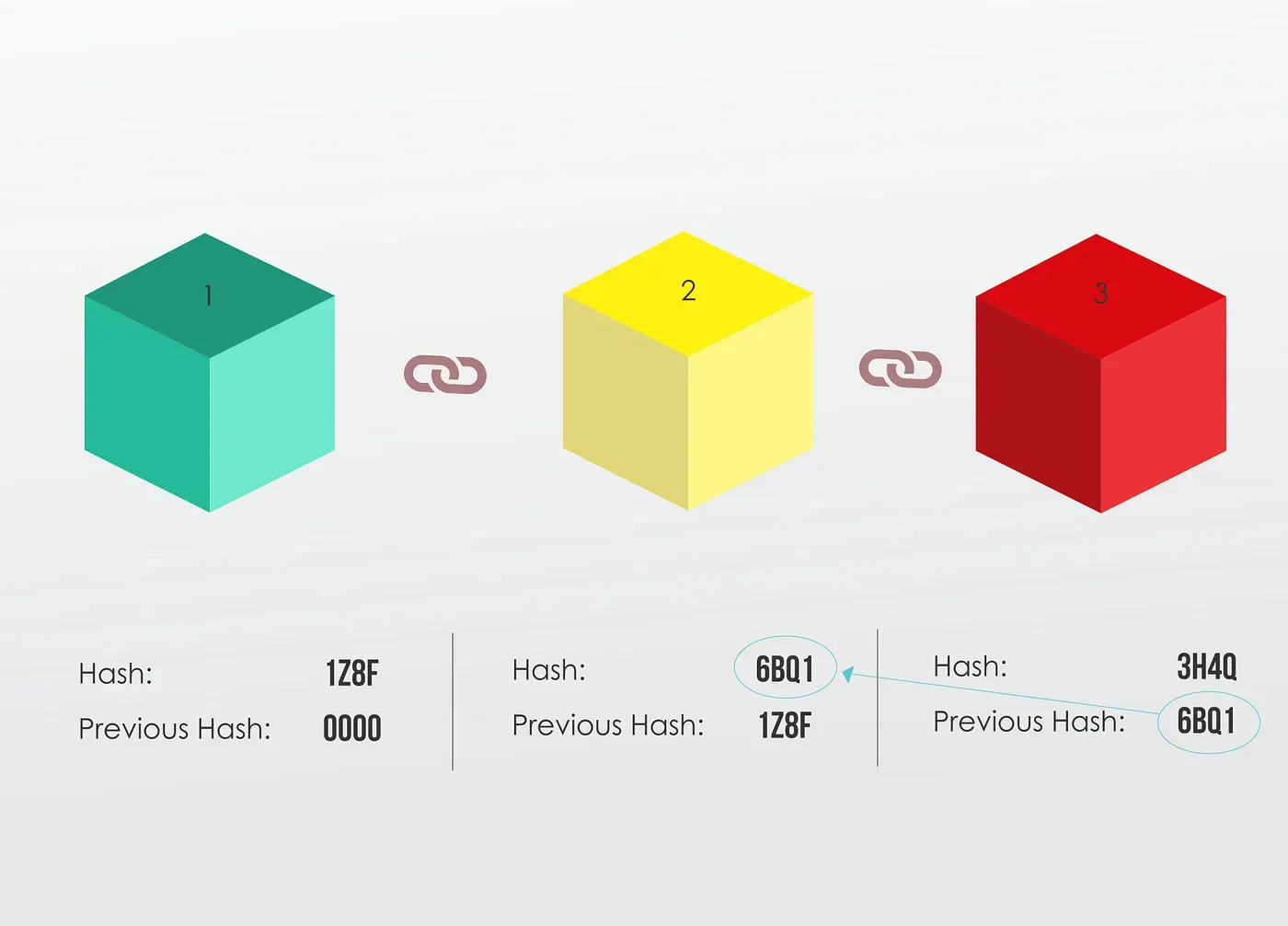
And block number 2 points to block number 1
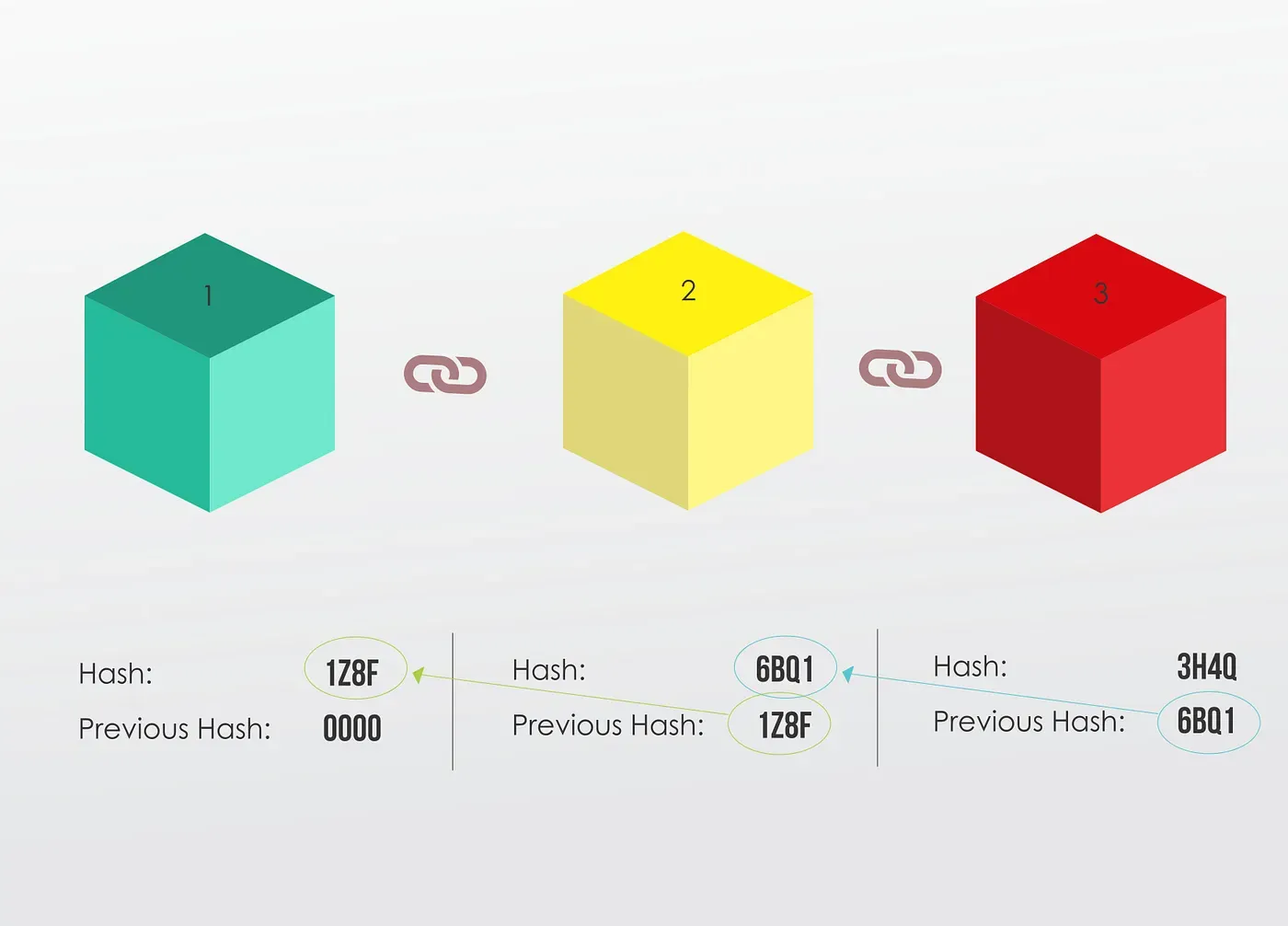
The first block is a bit special, it cannot point to a previous block, because it’s the first one, we call this block the Genesis Block.
Press enter or click to view the image in full size
Let’s say you tamper with the second block; that changes its hash as well.
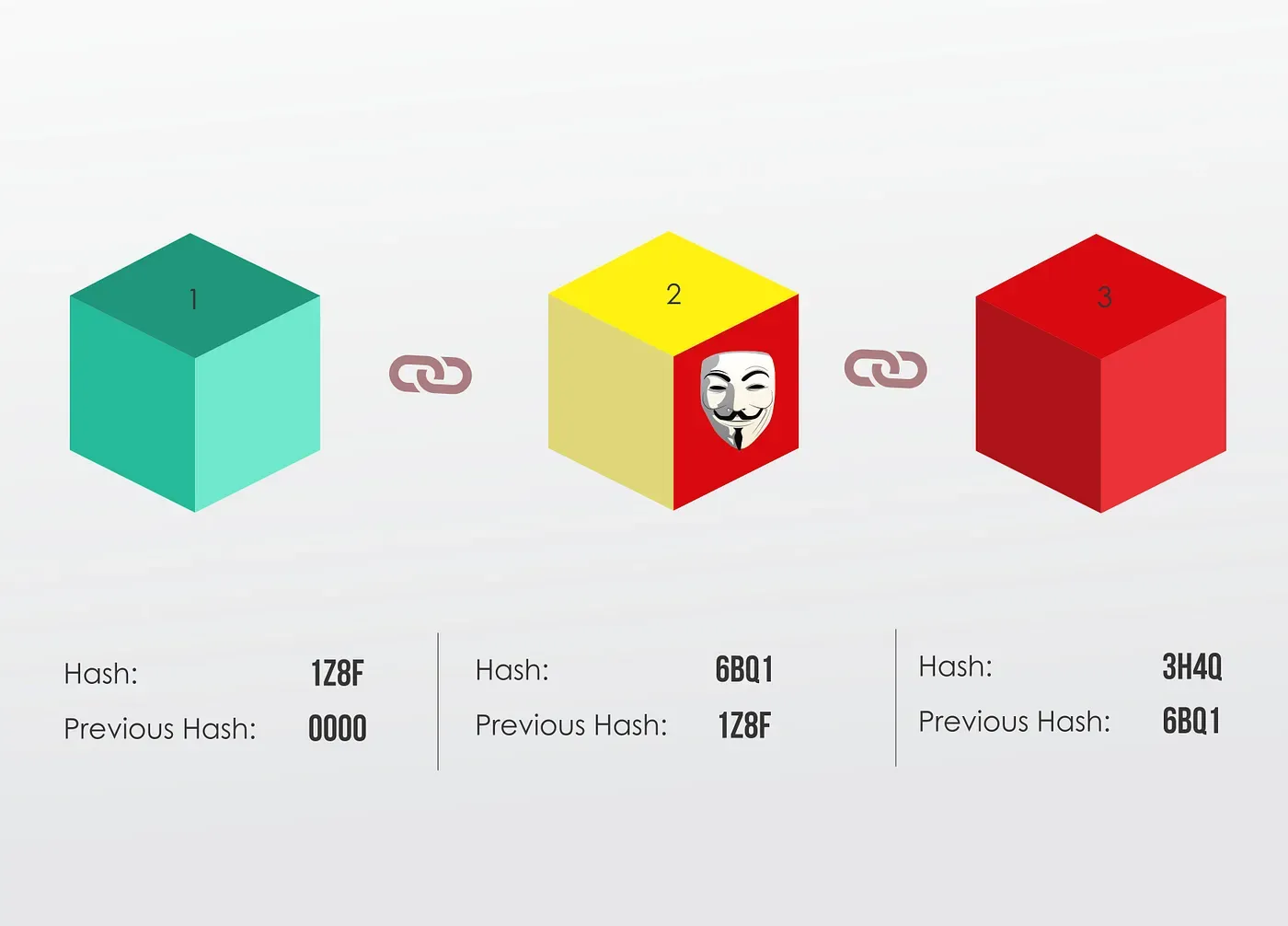
In turn, that will make block 3 and all following blocks invalid, because they no longer store a valid hash of the previous block.
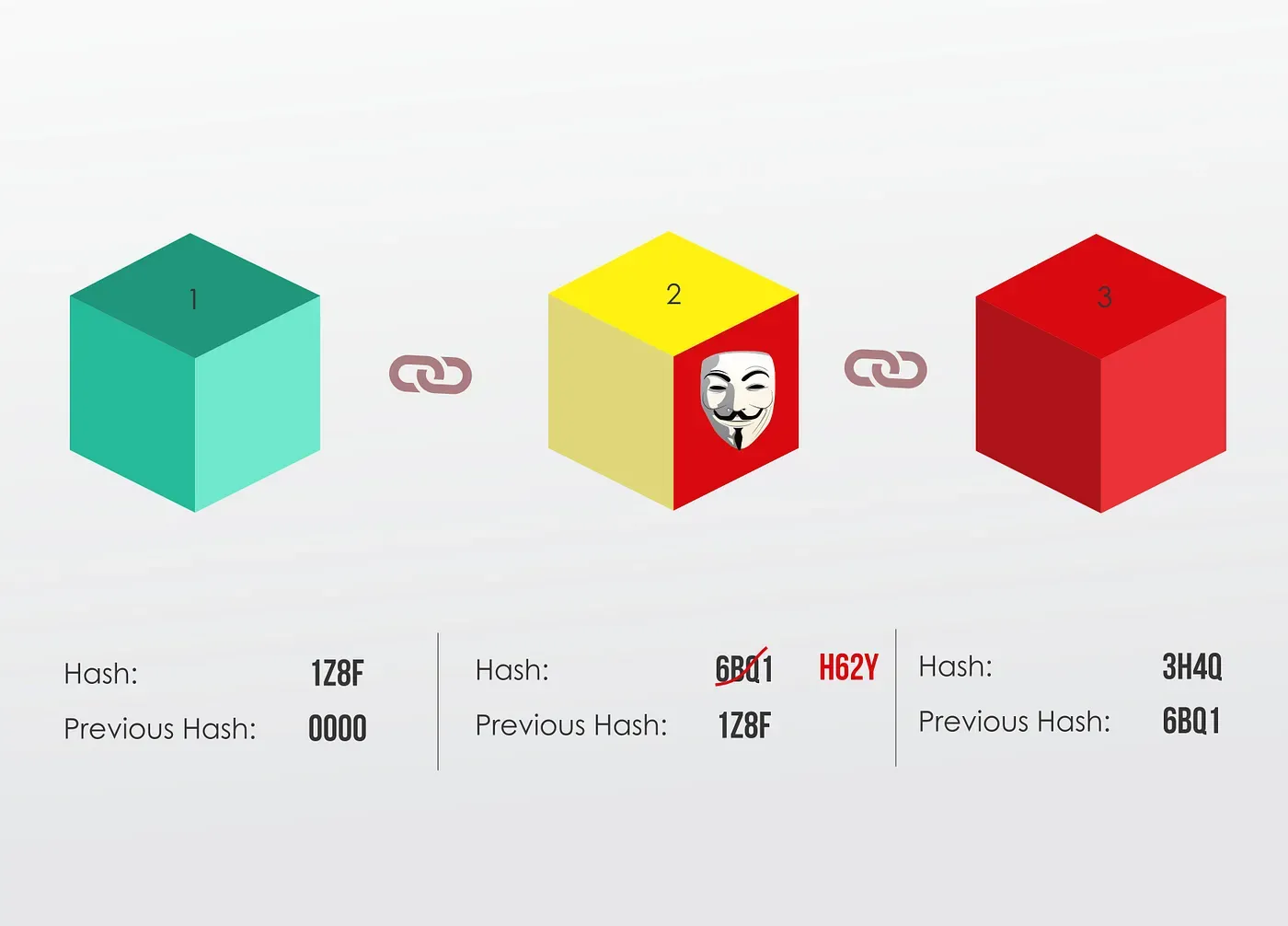
So changing a previous block will make all following blocks invalid.
How Does Blockchain Secure itself?
Using hashes is not enough to prevent tampering; computers these days are fast and can calculate hundreds of thousands of hashes per second.
You can effectively tamper with a block and recalculate all the hashes of other blocks to make your blockchain valid again.
To mitigate this, blockchains use a mechanism called “Proof-of-work.”
What is a Proof-of-work
This mechanism slows the creation of new blocks.

In bitcoins case, it takes about 10 mins to calculate the required proof-of-work and add a new block to the chain.
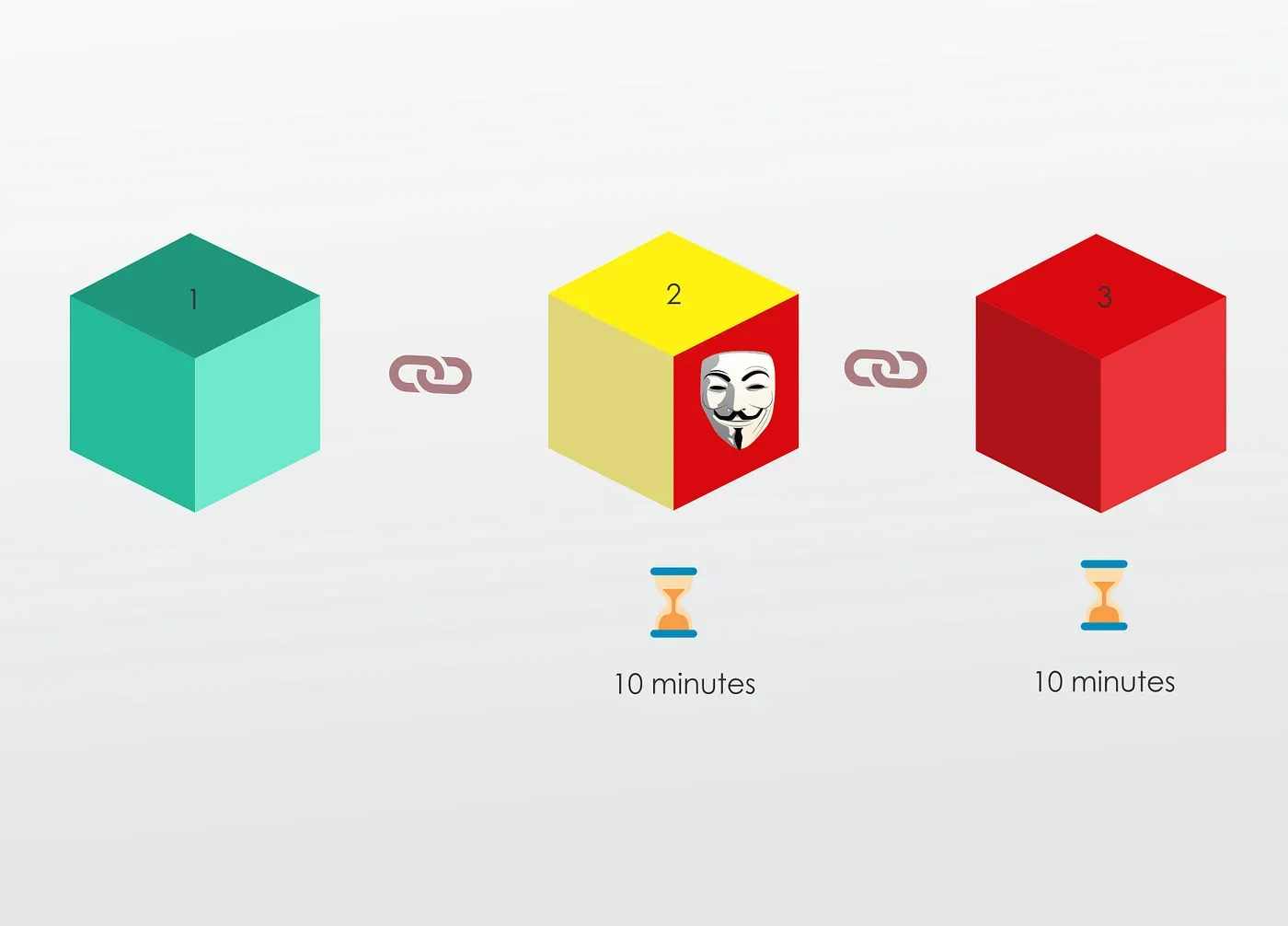
This mechanism makes it very hard to tamper with the blocks because if you tamper with one block, you’ll need to recalculate not just the hash but the proof-of-work for all the following blocks.
So the security of blockchain comes from its creative use of hashing and the proof-of-work mechanism.
There’s one more way that blockchain secures itself, and that is by being “Distributed”
Instead of using a central entity to manage a chain, blockchain uses a peer-to-peer (P2P) network, allowing anyone to join.
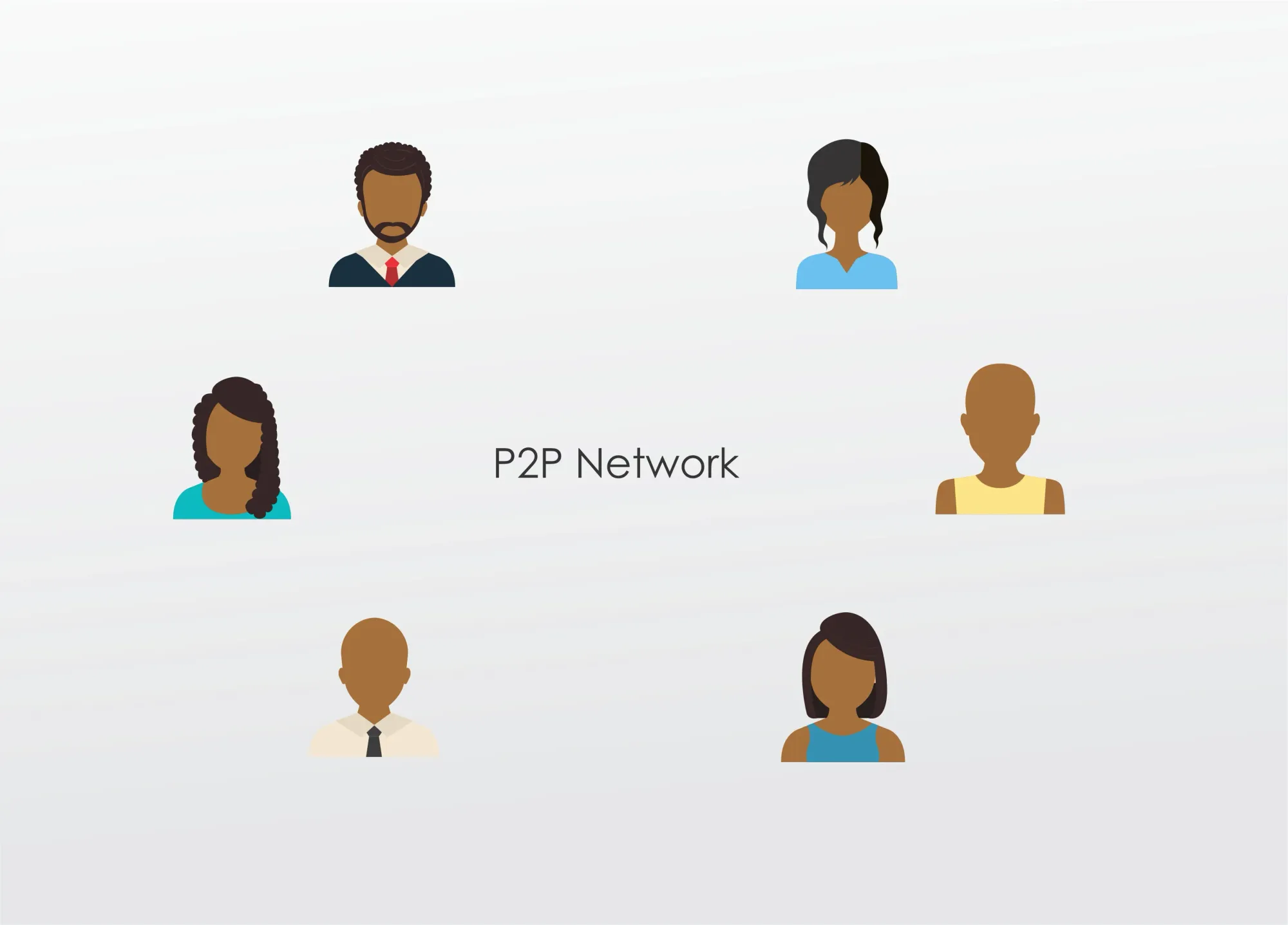
When someone joins this network, he gets a full copy of the blockchain.
The node can use this to verify that everything is in order.
When someone creates a new block, that block is sent to everyone on the network.
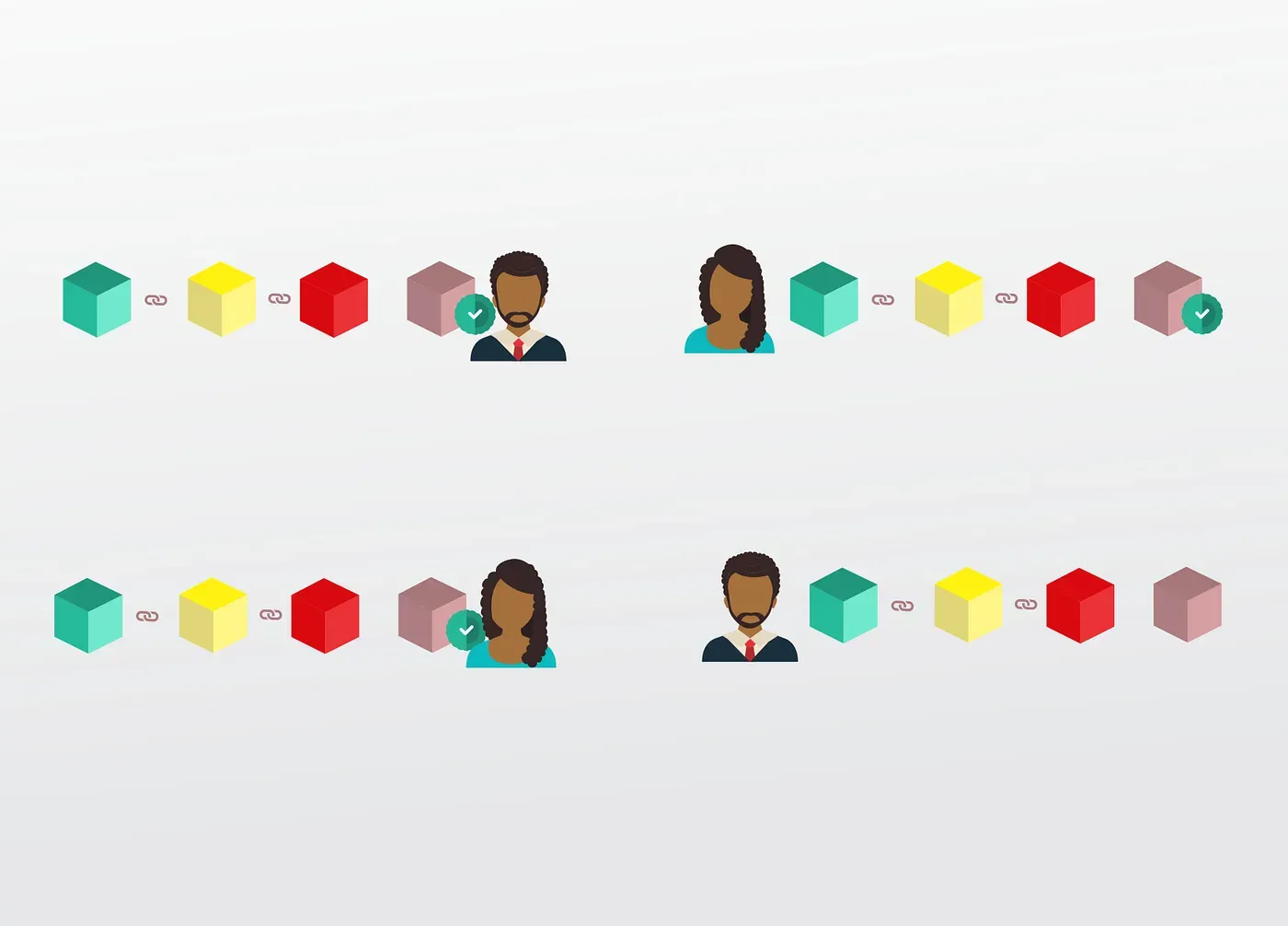
Each node on the P2P network then verifies the block to ensure it hasn’t been tampered with, and if everything checks out, each node adds it to its own blockchain.
All the nodes in this network Consensus blocks are valid and which aren’t.
Blocks that are tampered with will be rejected by other nodes in the network.

In other words, to successfully tamper with a blockchain, you’ll need to tamper with all the blocks on the chain, redo the proof-of-work for each block, and take control of more than 50% of the P2P network. Only then will your tampered block be completely accepted by everyone else. This is almost impossible to do.
Blockchains are almost constantly evolving; one of the most recent developments is the creation of “smart contracts”.
These contracts are simple programs stored on the blockchain that can automatically exchange coins under certain conditions.
Some Useful Applications of Blockchain
The creation of blockchain technology sparked interest among many people. Soon, others realize that this technology can be used for other things, like;
Storing medical records
Creating a digital notary
Collecting taxes
Conclusion
Phew!! That was a lot of information to digest. I hope this article has helped you understand this bearish technology and prepared you for a good discussion with your friends about Blockchain. Blockchain and its potential in Africa.
If you enjoyed reading this, please click and hold “Claps” below and help your friends find it by sharing it with them. Thank You! :)